IAM (Identity and Access Management)
- IAM 이란 AWS Resources 접근 권한을 관리하는
Global Service - Root Account 는 AWS 계정 생성 시에 기본으로 생성되고 AWS 계정 생성에만 사용
IAM Users & User Groups
- User 는 하나의 조직 내 사용자에 해당하며 필요하다면 Group 으로 묶을 수 있음
- User 는 0~10개의 Group 에 속할 수 있음
- Group 은 User 만을 포함할 수 있으며 Group 을 포함하는 것은 불가능
최소 권한 원칙을 바탕으로 AWS 를 사용하게끔 하기 위해서 IAM User 와 Group 을 사용- User 또는 Group 은 JSON 형식으로 이루어진 IAM Policy 를 할당 받을 수 있음
IAM User 생성
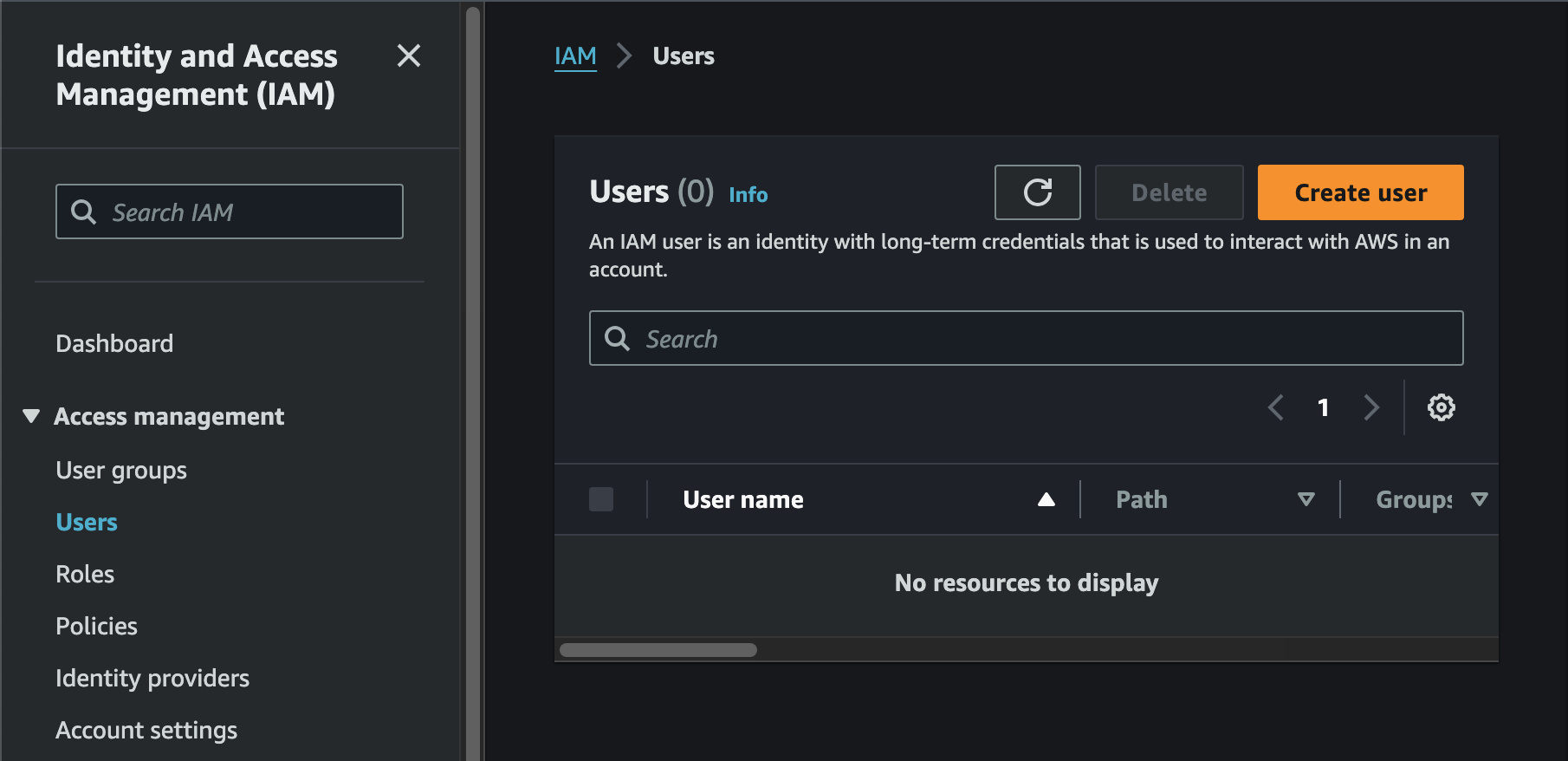
- AWS Management Console 에서 IAM → Users → Create user
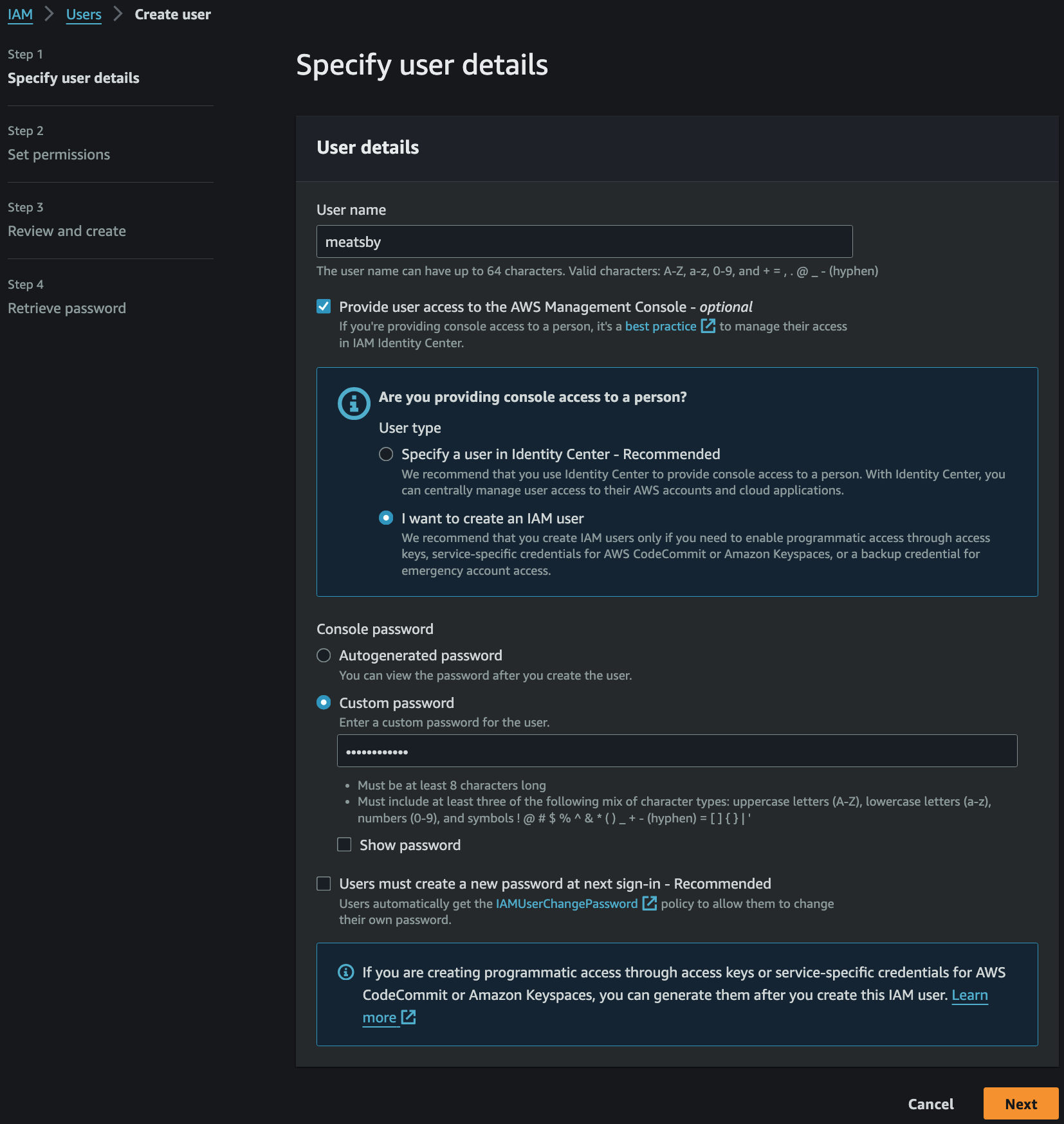
Provide user access to the AWS Management Console활성화를 통해 User 에게 AWS Management Console 이용 권한 부여Console password를 Custom password 로 설정해서 User 생성- 타인을 위한 IAM User 생성 시
Autogenerated password+User must create a new password at next sign-in으로 비밀번호 재설정 의무화
- 타인을 위한 IAM User 생성 시
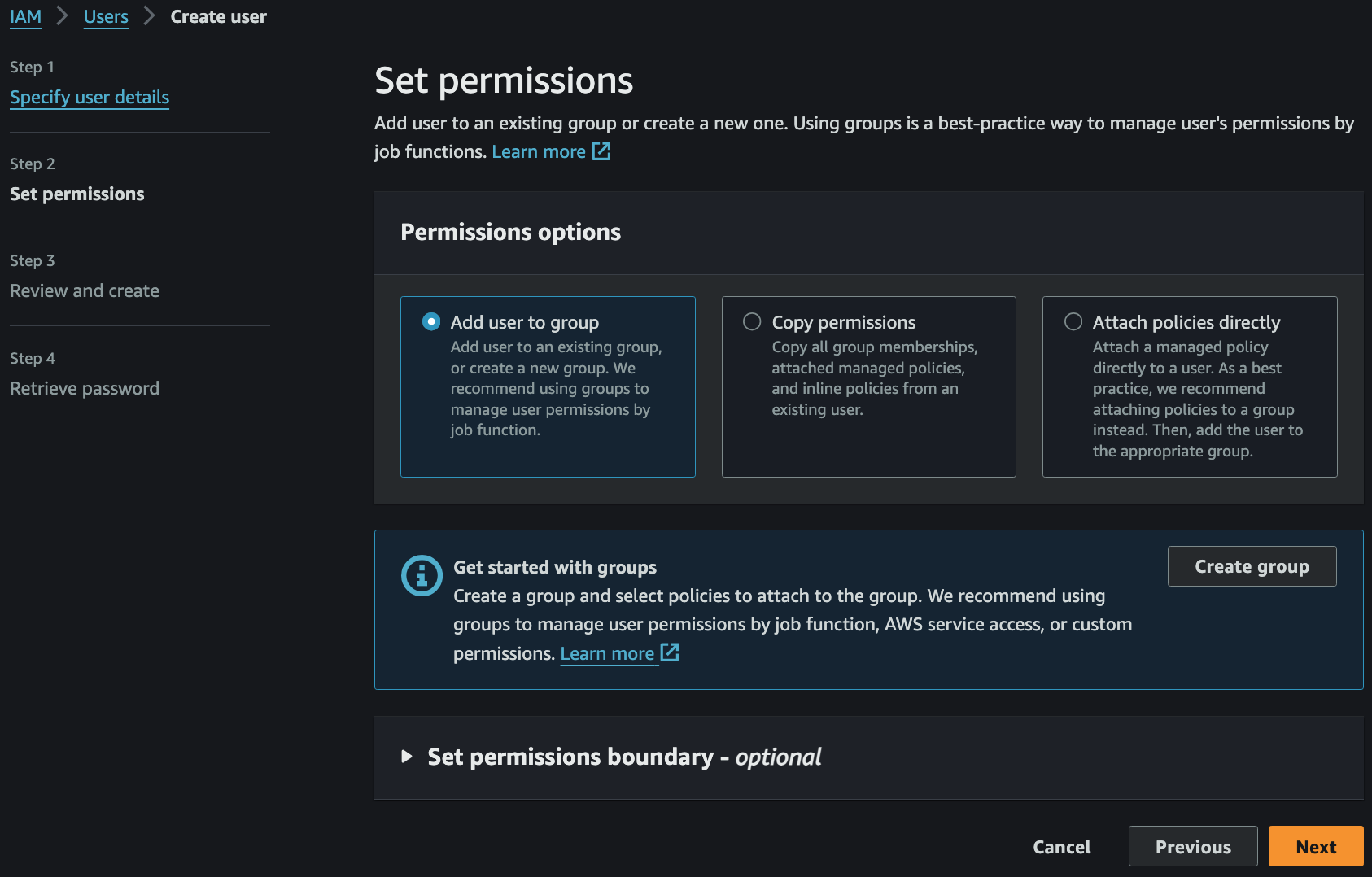
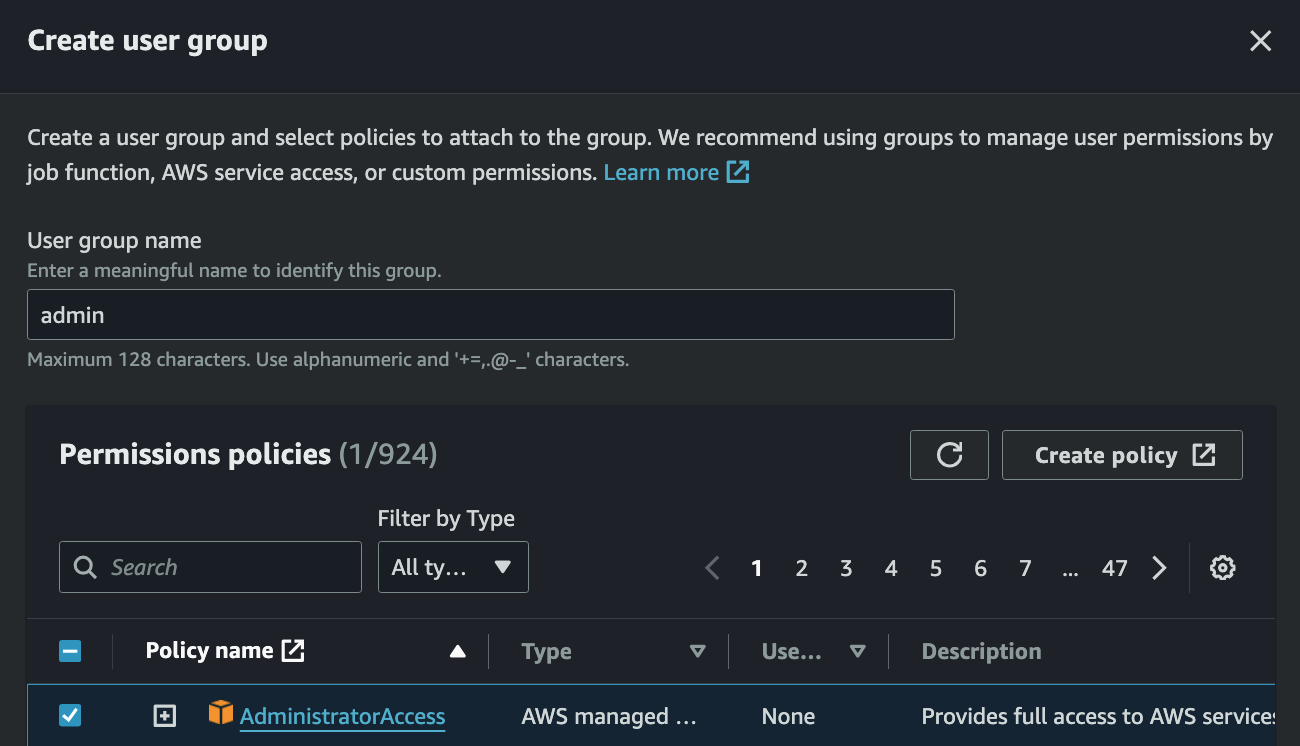
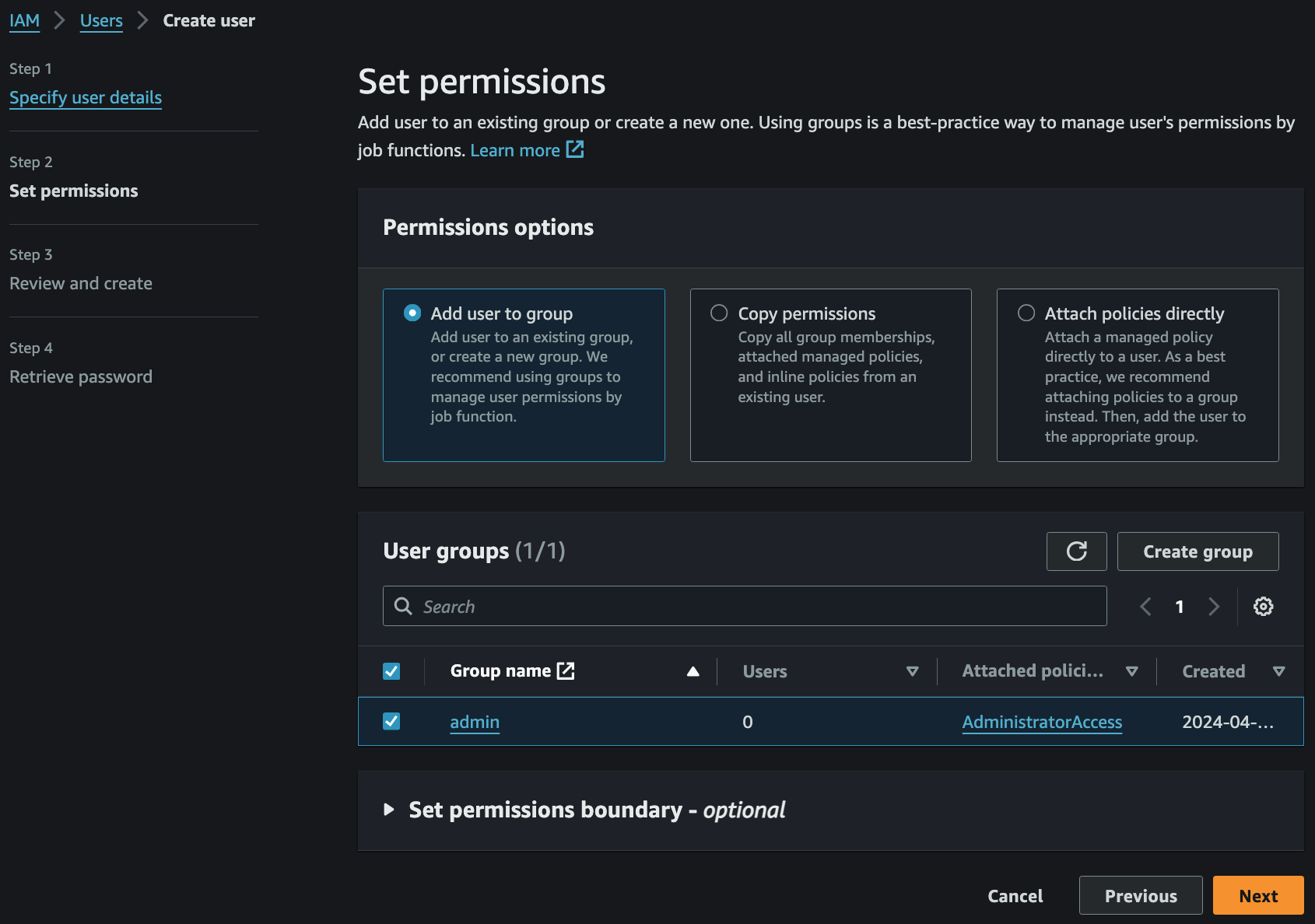
- Create group 으로 User 가 속할 Group 을 만들면서 동시에 Permission policies 까지 할당
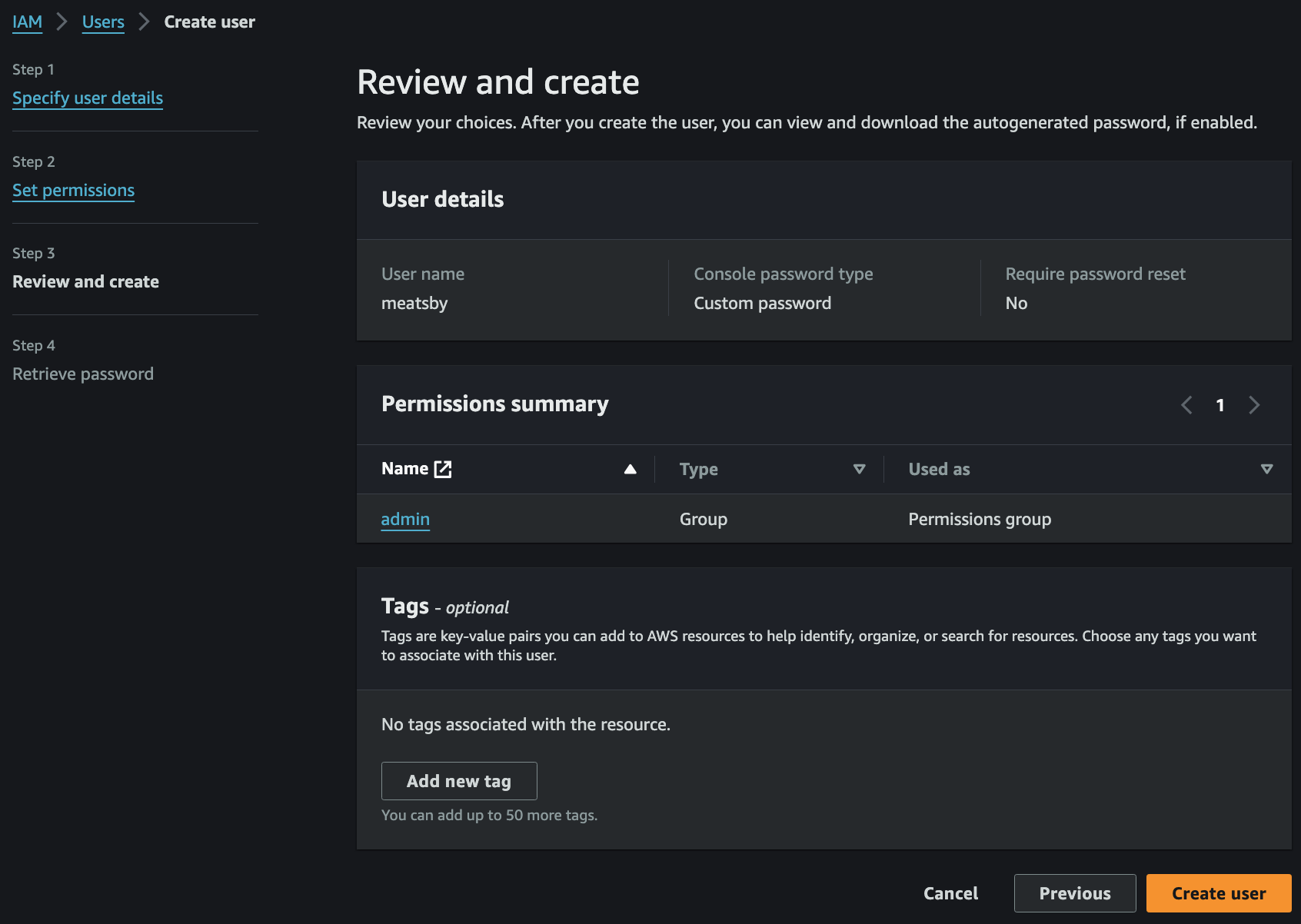
- 마지막 Review 후 Create user 클릭 시 User 생성 완료
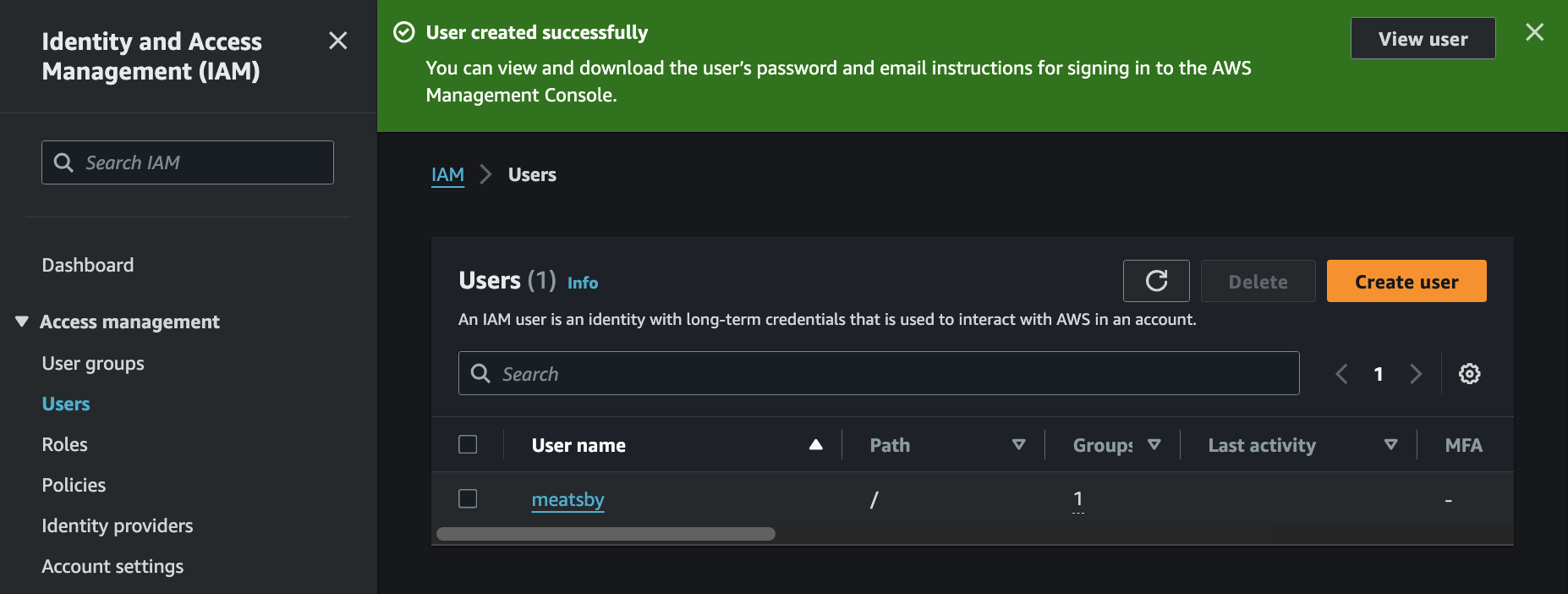
- Users 로 다시 돌아와보면 User 가 성공적으로 생성되어있는 것을 확인 가능
IAM User Access Key for AWS CLI
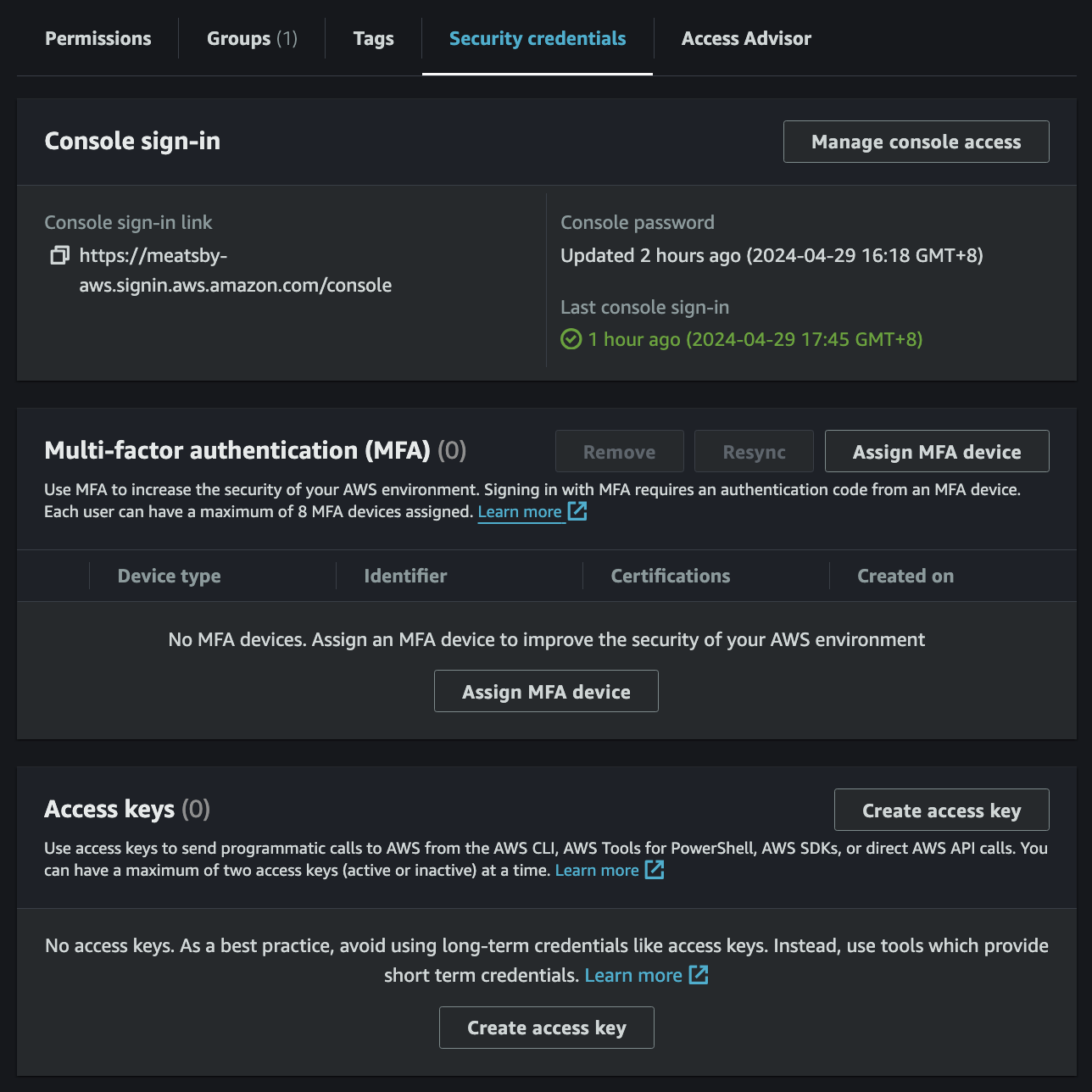
- AWS Management Console 에서 IAM → Users → User 선택 → Security credentials 탭 → Access keys 에서
Create access key
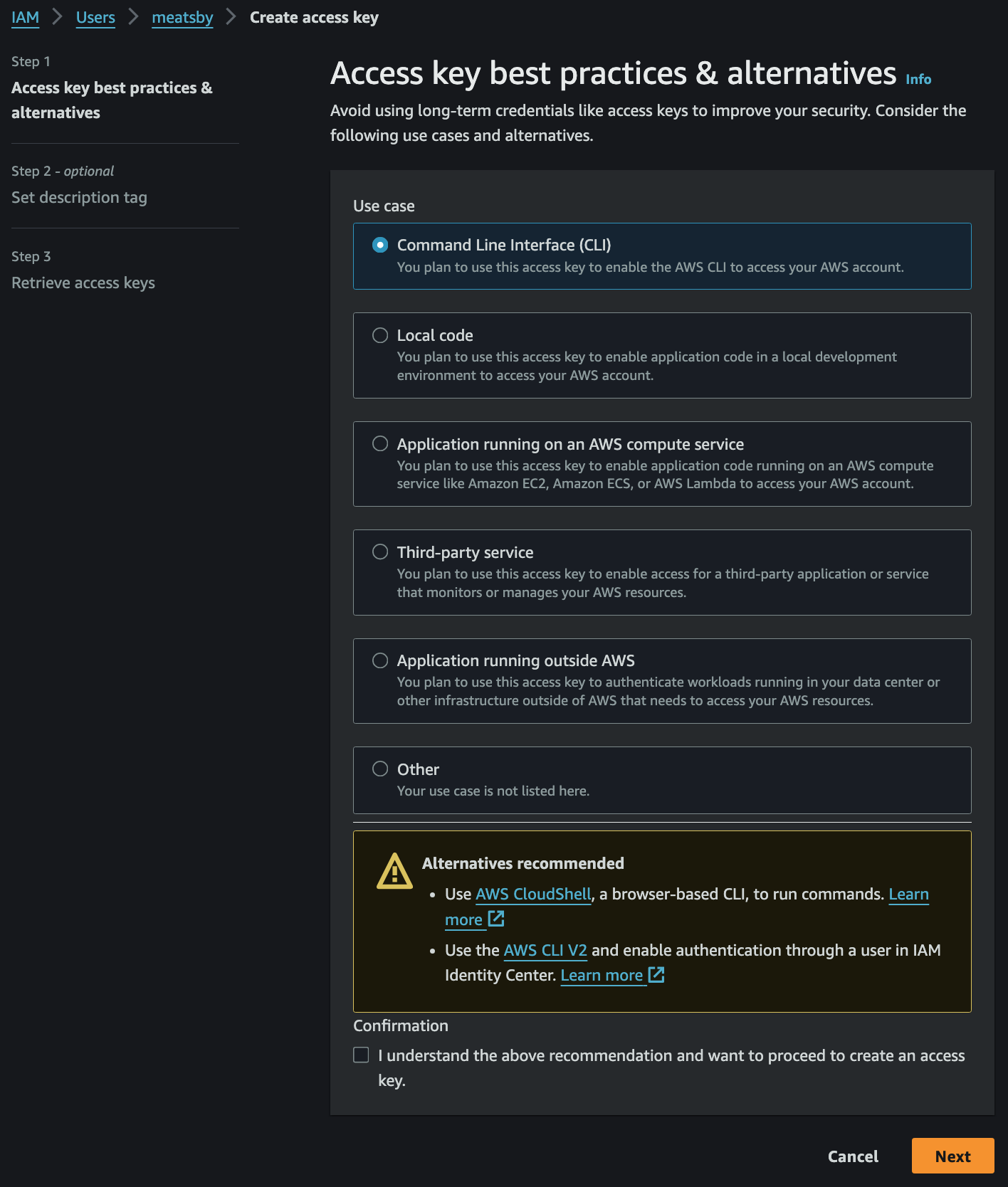
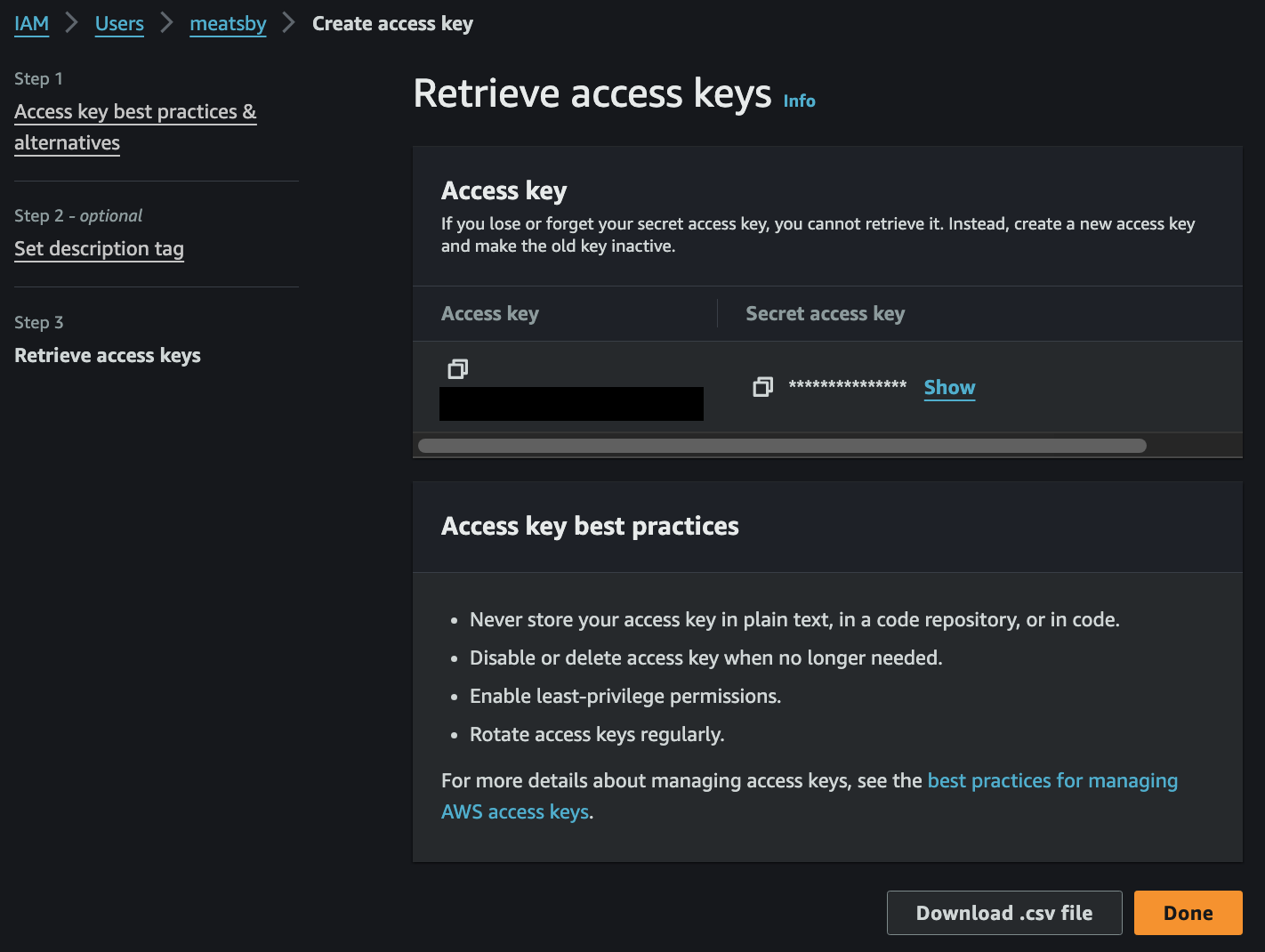
- CLI 선택후 마지막 화면이 Access Key 와 Secret Access Key 를 저장할 수 있는 유일한 시간
$ aws configure
AWS Access Key ID [None]: ACCESS_KEY
AWS Secret Access Key [None]: SECRET_ACCESS_KEY
Default region name [None]: ap-east-1
Default output format [None]:
aws configure명령어 입력 후 위와 같이 설정하면 CLI 로 AWS API 를 사용 가능- 단, EC2 인스턴스와 같이 타인이 접속할 수 있는 머신에서 이 방법을 쓰면 타인이 인스턴스에 입력된 자격 증명 정보를 회수할 수 있기 때문에 best practice 가 아님
- 따라서 EC2 에서 AWS API 를 사용하길 원할 경우 IAM Role 을 지정하는게 best practice
IAM Policies
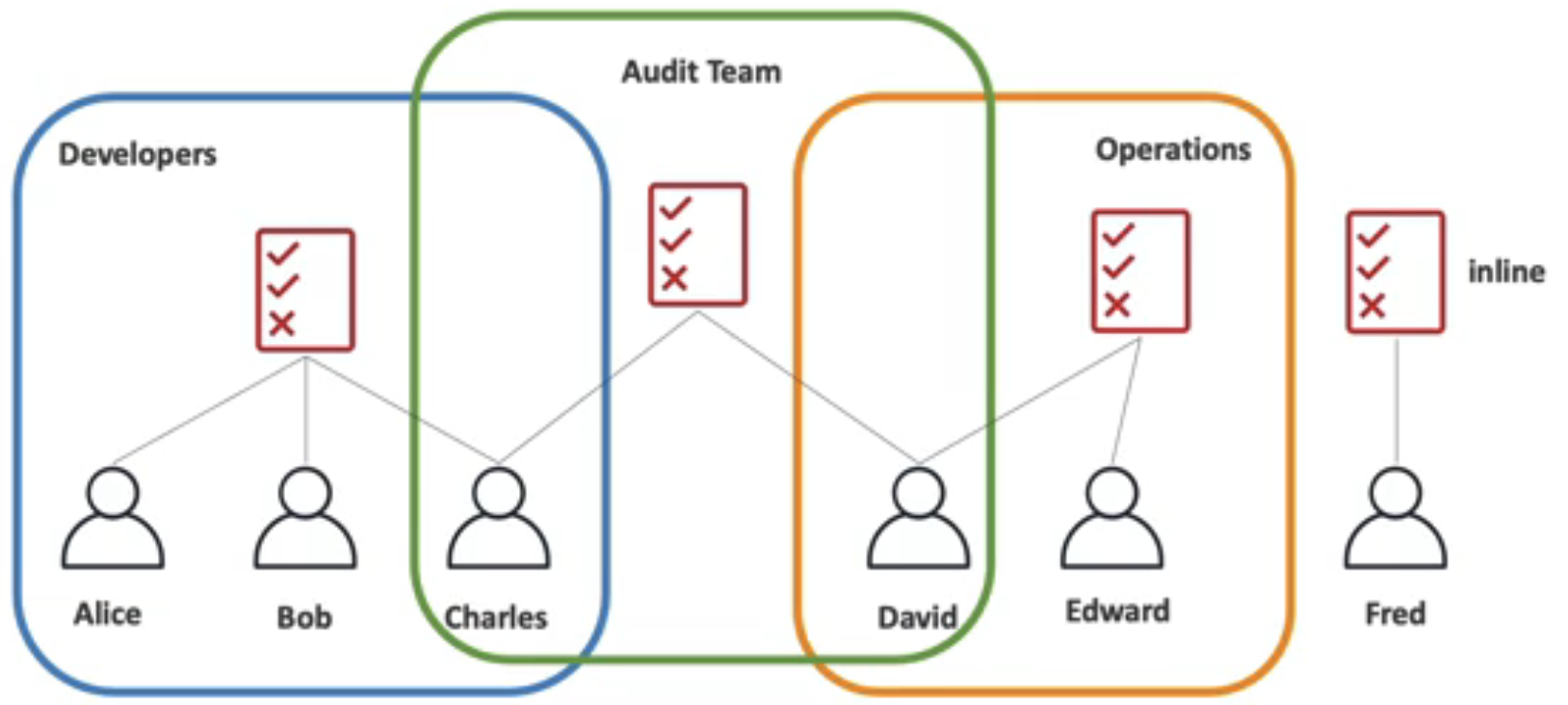
- IAM Policy is a JSON document that allows or denies permissions to AWS resources
- Follow the security
principle of least privilegewhen granting permissions - IAM Policy can be assigned to User Groups or User itself with inline-policy
- Follow the security
IAM Policies Structure
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"iam:GenerateCredentialReport",
"iam:GenerateServiceLastAccessedDetails",
"iam:Get*",
"iam:List*",
"iam:SimulateCustomPolicy",
"iam:SimulatePrincipalPolicy"
],
"Resource": "*"
}
]
}Version: Policy language version, mostly “2012-10-17”Id: Identifier for the policy (Optional)Statement: One or more individual statementsSid: Identifier for the statement (Optional)Effect:AlloworDenyPrincipal: Account/User/Role to which this policy applied toAction: List of actions this policy allows or deniesResource: List of resources to which the action applied toCondition: Conditions for when this policy is in effect (Optional)
IAM Policies 종류
- Identity-based policies: IAM Users, IAM User Groups, IAM Roles 에 적용하는 Policy
- AWS Managed Policy: AWS 에서 기본으로 제공하는 Policy, 여러 계정에서 동일한 Policy 사용 가능
- AWS Customer Managed Policy: 사용자가 생성한 Custom Policy, 해당 Policy 가 생성된 계정만 사용 가능
- AWS Inline Policy: 명시적으로 할당하는 1대1 Policy, 보통 Managed 를 사용하길 권장, 명시적으로 특정 사용자에게 특정 권한을 부여하고 싶을 경우에 사용하면 유용
- Resource-based policies: AWS Resource 에 적용하는 Policy, 대표적으로 S3 Bucket Policy 가 있음
- Permissions boundaries
- Organizations SCPs
- Access control lists - ACLs
- Session policies
IAM Roles
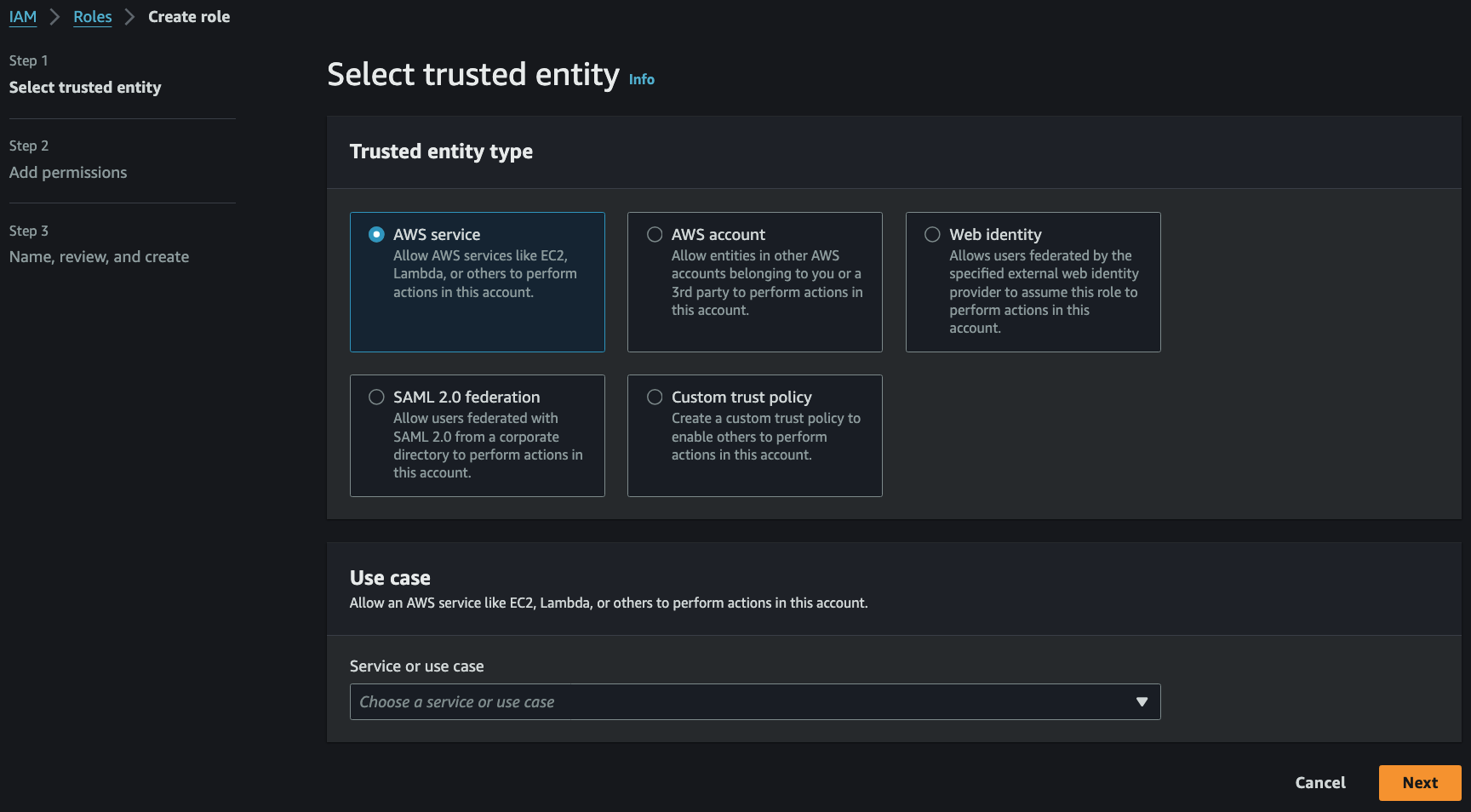
- IAM Role 은 AWS Services 를 위한 IAM User 라고 생각할 수 있음
- An identity that you can assume to gain
temporary accessto permissions - Ideal for situations in which access to services or resources needs to be granted
temporarily, instead of long-term - To grant users in one AWS account access to resources in another AWS account
- IAM Users 의 권한을 쉽게 관리하기 위해 IAM User Groups 를 사용하는데, 권한이 다양해지면 관리가 복잡해지고 이를 해결하기 위해 IAM Roles 를 사용
- User Group 에 권한을 바로 부여하는 대신, Role 을 만들고 User 또는 User Group 에 할당
- 임시 세션토큰을 발급하여 일시적인 권한을 위임
IAM Security Tools
IAM Credential Reports (account-level)
- AWS Management Console 에서 IAM → Credential report → Download Report
- A report that lists all account’s users and the status of their various credentials
IAM Access Advisor (user-level)
- AWS Management Console 에서 IAM → Users → User 선택 → Access Advisor 탭
- 어떤 AWS Services 에 마지막으로 접근했는지 확인 가능
- 접근하지 않는 Resources 는 제한하여
principle of least privilege를 지킬 수 있음
- 접근하지 않는 Resources 는 제한하여
IAM 권한 검증 절차
IAM User 가 S3 를 사용하고 싶은 경우
- IAM User 에게 S3 사용 Policy 가 부여되었는가?
- IAM User 가 속한 IAM User Group 에 S3 사용 Policy 가 부여되었는가?
- IAM User 에게 위임된 Role 에 S3 사용 Policy 가 부여되었는가?
- OK 또는 Fail
Lambda 가 S3 를 이용하고 싶은 경우
- Lambda 에 S3 사용 Role 이 부여되었는가?
- OK 또는 Fail
- IAM Access Analyzer
Identifieswhether an Amazon S3 bucket or an IAM role has beensharedwith anexternal entitysuch asanother AWS account- Checks access policies and offers actionable recommendations to help users set secure and functional policies
- IAM Credential Report
- To
auditits password and access key rotation details forcompliancepurposes
- To
- AWS Security Token Service (STS)
- To request
temporary,limited-privilegecredentials for users
- To request
IAM Conditions
aws:SourceIp
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "*",
"Resource": "*",
"Condition": {
"NotIpAddress": {
"aws:SourceIp": [
"192.0.2.0/24",
"203.0.113.0/24"
]
}
}
}
]
}- Restrict the client IP from which the API calls are being made
aws:RequestedRegion
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "*",
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:RequestedRegion": [
"eu-central-1",
"eu-west-1"
]
}
}
}
]
}- Restrict the Region the API calls are made to
ec2:ResourceTag
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*",
"Condition": {
"StringEquals": {
"aws:ResourceTag/Project": "DataAnalytics"
}
}
}
]
}- Restrict based on tags
aws:MultiFactorAuthPresent
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Action": "*",
"Resource": "*",
"Condition": {
"BoolIfExists": {
"aws:MultiFactorAuthPresent": false
}
}
}
]
}- To force MFA
IAM for S3
s3:ListBucketpermission applies toarn:aws:s3:::test- Bucket level permission
s3:GetObjectpermission applies toarn:aws:s3:::test/*- Object level permission
Resource Policies & aws:PrincipalOrgID
aws:PrincipalOrgIDcan be used in any resource policies to restrict access to accounts that are members of an AWS Organization
IAM Role vs Resource-Based Policies
- In Cross-Account situation
- Resource-Based Policy can be attached to a resource (e.g. S3 bucket policy)
- OR use a Role as a proxy
- When using Assume Role, original permissions will not work
- When using Resource-Based Policy, resource allows given permissions
Amazon EventBridge - Security
- When a rule runs, it needs permissions on the target
- Resource-Based Policy: Lambda, SNS, SQS, CloudWatch Logs, API Gateway, …
- IAM Role: Kinesis Stream, Systems Manager Run Command, ECS task, …
IAM Permission Boundaries
- IAM Permission Boundaries are supported for users and roles (not group)
- Advanced feature to use a managed policy to set the maximum permissions an IAM entity can get
- Can be used in combinations of AWS Org SCP